Listen to the podcast :
Outsourcing software development to India is a strategic imperative for global enterprises. The country presents an unparalleled talent pool, offering cost-efficiency and deep technical expertise that drives innovation. However, outsourcing software development in this cross-border collaboration, while yielding significant benefits, inherently involves sharing sensitive business data, proprietary source code, and customer information.
For any international entity, the paramount concerns when they hire dedicated developers in India are ensuring robust data security and establishing absolute IP protection. These are not merely administrative tasks; they are critical risk mitigation strategies that protect your core competitive advantage.
This informational guide is carefully crafted to equip you with the essential technical, legal, and operational checks required to safeguard your Intellectual Property (IP) and maintain an uncompromising security posture throughout your outsourcing journey. Understanding these checks is crucial before the first line of code is written.
Ready to hire developers with strong data and IP safeguards? Talk to WeblineIndia today.
Data Security and IP Protection are Two Crucial Factors
It is essential to first distinguish between the two distinct, yet interconnected, aspects of protection: data security and IP protection.
Data Security refers to the comprehensive measures, controls, and policies implemented to shield data—specifically Sensitive Personal Data (SPD), Personally Identifiable Information (PII), and confidential business data—from unauthorized access, misuse, corruption, or theft, whether the data is at rest or in transit. This is fundamentally a technical and procedural challenge, involving firewalls, encryption, and access management. When you hire dedicated developers in India, you must verify their operational excellence in this domain.
IP Protection, conversely, focuses on the legal and contractual frameworks that ensure the client retains exclusive ownership rights over all created deliverables. This includes the source code, technical specifications, database schema, design assets, and proprietary algorithms developed during the engagement. This is a contractual challenge, designed to prevent the vendor or developer from claiming or misusing the final product. A strong IP protection strategy is what prevents your new product from becoming your competitor’s next offering.
Addressing both pillars requires a holistic strategy encompassing legal frameworks, advanced technical infrastructure, and strict organizational security policies.
Legal and Contractual Due Diligence: Securing Your Ownership
Your contract is the foundation of your protection strategy. It must be explicit, comprehensive, and legally enforceable across jurisdictions. This is the first area to focus on when you plan to hire dedicated developers in India.
The Stringent Non-Disclosure Agreement (NDA)
A robust Non-Disclosure Agreement (NDA) must be executed before any proprietary information is exchanged. This agreement serves as the contractual shield for your proprietary information.
- Key Definition: Ensure the NDA defines “Confidential Information” broadly. It should encompass not just technical artifacts like source code and architecture diagrams, but also commercial data, pricing models, market strategies, and proprietary knowledge (trade secrets).
- Developer Commitment: It is not sufficient for only the vendor company to sign the NDA. Every individual dedicated developer and team member who will have access to your project assets must sign a back-to-back NDA with the vendor, thereby creating a clear, auditable, and enforceable contractual chain down to the individual contributor.
- Post-Termination Obligation: The agreement must stipulate a significant period for confidentiality obligations to survive the termination of the contract, typically ranging from two to five years, or be designated as perpetual for genuine trade secrets. Indian law is generally supportive of enforcing these clauses, and a breach allows for remedies like injunctive relief and monetary damages.
Comprehensive IP Assignment and “Work-for-Hire” Clauses
This is the single most critical check for IP protection. Under common law principles, an independent contractor often retains the copyright to their creative work unless explicitly assigned. Your contract must decisively override this default.
- Unequivocal Assignment: The contract must include an unambiguous IP assignment clause that states all Intellectual Property created, developed, or contributed by the dedicated developers under the engagement—including the final source code, libraries, technical specifications, user interfaces, documentation, and all derivative works—is deemed “Work-for-Hire” and is immediately and exclusively owned by the client. The language should clearly detail the transfer of all economic and moral rights.
- Indemnification Clause: Insert a clause requiring the vendor to indemnify you against any third-party claims of IP protection infringement. This is essential to ensure that the developers are not using open-source components incorrectly or integrating pre-existing code for which they do not possess the necessary licenses, thereby protecting your final product from legal challenge.
- Ownership of Pre-existing IP: Clearly delineate what is client-owned pre-existing IP (what you bring to the table) versus the new IP created. If the vendor utilizes any of its own proprietary frameworks or tools, the contract must explicitly grant you a perpetual, non-exclusive, royalty-free license to use, modify, and distribute those components within your final application.
Clear Jurisdiction and Dispute Resolution
When you are hiring Indian developers, your contract involves international legal concerns. Defining how disputes will be resolved is a critical element of IP protection.
- Governing Law: Specify the law that governs the contract (e.g., your home country’s law, or a mutually agreed international standard).
- Resolution Mechanism: Include a binding arbitration clause, often preferred over litigation in civil courts for faster resolution. For effective enforcement against the Indian entity, specifying arbitration under Indian laws (such as the Arbitration and Conciliation Act) in a major Indian commercial hub can prove more practical.
Technical and Procedural Checks to Fortify Data Security
Contractual clauses are the legal skeleton; the vendor’s operational procedures and technical infrastructure are the muscle that provides real-time data security. Due diligence here must be rigorous.
Security Certifications and Audits
A certified vendor provides demonstrable evidence of security maturity. These certifications signify adherence to best-in-class security management systems.
- International Standards: Demand proof of compliance with internationally recognized security standards. The most important is ISO/IEC 27001:2022 (Information Security Management System), which ensures the vendor has documented, implemented, maintained, and continually improved a risk-based security system. Furthermore, look for SOC 2 Type II reports, which validate the internal controls related to security, availability, processing integrity, confidentiality, and privacy over a period of time.
- Third-Party Audits: Require evidence of regular security audits and penetration testing conducted by independent, accredited third-party firms. Review the remediation processes they have in place to address identified vulnerabilities.
Physical and Logical Access Control
Preventing unauthorized access, particularly insider threats, is central to data security.
- Physical Security Measures: The vendor’s premises must have stringent physical controls, including 24/7 security monitoring, CCTV surveillance, and multi-layered access restrictions (e.g., biometric authentication) to development areas.
- Data Loss Prevention (DLP): Institute a strict DLP policy. Developers should operate on company-managed machines with disabled external ports (USB, optical drives) and restricted network access. This prevents unauthorized data transfer or exfiltration of code and documents, essential for effective IP protection. Personal devices and external storage media should be strictly prohibited in the development zones.
- Role-Based Access Control (RBAC) and Principle of Least Privilege (PoLP): Implement granular access controls. Developers should only be granted access to the minimal set of resources (source code repositories, development servers, client environments, databases) strictly necessary for their specific roles. Access logs must be maintained for all critical systems, providing an Audit Trail for forensic analysis in case of a breach of data security.
- Multi-Factor Authentication (MFA): Mandatory MFA should be enforced for all logins to project repositories (Git/SVN), cloud provider services (AWS, Azure, GCP), internal project management tools, and communication channels. This significantly reduces the risk of credential theft.
Secure Development and Encryption Practices
A secure product begins with a secure process. The vendor must embed data security into their Software Development Lifecycle (SDLC).
- Encryption Protocols: All sensitive data must be encrypted at all stages. This includes Data-at-Rest (e.g., using AES-256 encryption for databases and file storage) and Data-in-Transit (e.g., enforcing TLS/SSL protocols for all communication, APIs, and data transfer channels).
- Secure Coding Standards: Ensure the development team adheres to industry best practices, such as the OWASP Top 10 for application security. Demand evidence of regular Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) throughout the development sprints.
- Secure Version Control Systems: All source code and sensitive configuration files must reside in a secure, centralized Version Control System (VCS), such as a dedicated corporate instance of Git or Subversion, with highly restrictive access rights. This provides a clean, trackable, and auditable history of the Intellectual Property.
Need a team that follows strict security, compliance, and coding standards? Connect with us.
Compliance and Regulatory Landscape in India
India’s legal ecosystem is actively strengthening its regulatory framework for data security, making it an increasingly secure location to hire dedicated developers in India. A reputable partner will be compliant with both local and international laws.
The IT Act, 2000, and SPDI Rules
The foundational legal framework is the Information Technology Act, 2000 (IT Act) and the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011 (SPDI Rules). These regulations mandate that any corporate entity collecting, processing, or storing “Sensitive Personal Data or Information” must implement “reasonable security practices.”
- Liability: Section 43A of the IT Act makes a body corporate liable to pay compensation to the affected party if its negligence in implementing reasonable security practices leads to a wrongful loss or gain due to a data breach. This provision provides significant legal recourse for clients concerned about data security.
The Digital Personal Data Protection Act, 2023 (DPDP Act)
The recent enactment of the Digital Personal Data Protection Act, 2023 (DPDP Act), significantly elevates India’s commitment to data privacy, moving its standards closer to the global benchmark of GDPR.
- New Obligations: The DPDP Act introduces heightened requirements for consent, notice, and accountability for entities processing digital personal data. It imposes strict compliance obligations on both the Data Fiduciary (the client) and the Data Processor (the vendor).
- Vendor Compliance: Your agreement must explicitly require the vendor to comply with the DPDP Act and any other relevant international frameworks (like HIPAA for healthcare data or GDPR for EU citizen data) relevant to your project. Furthermore, the vendor must have a formal, tested Incident Response Plan that includes immediate notification to you upon discovery of any potential or actual breach affecting your data security.
Data Security and IP Protection Regulations at a glance
Here is the list from this blog that mentioned myriad rules, regulations, compliances, and a set of standards used for data security and IP protection, especially in India.
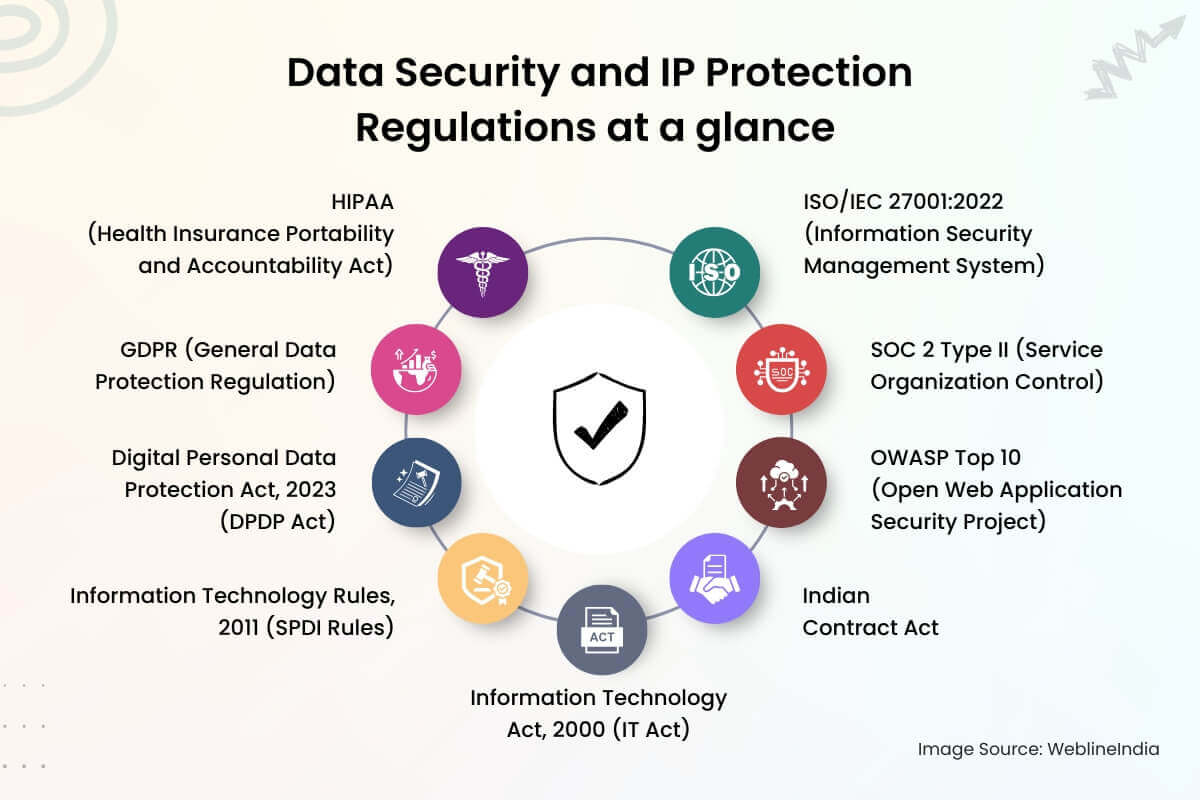
- ISO/IEC 27001:2022 (Information Security Management System): An international standard for managing information security risks systematically.
- SOC 2 Type II (Service Organization Control): Reports that validate a service organization’s internal controls related to security, availability, processing integrity, confidentiality, and privacy over a period of time.
- OWASP Top 10 (Open Web Application Security Project): A standard list of the ten most critical web application security risks.
- Indian Contract Act: The primary legislation governing contracts and the enforceability of agreements like NDAs in India.
- Information Technology Act, 2000 (IT Act): India’s primary law dealing with cybercrime and e-commerce, holding companies liable for negligence in data security.
- Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011 (SPDI Rules): Mandates specific security practices for handling sensitive personal data in India.
- Digital Personal Data Protection Act, 2023 (DPDP Act): India’s latest, comprehensive law governing the processing of digital personal data, similar to GDPR.
- GDPR (General Data Protection Regulation): The EU regulation protecting the data and privacy of EU citizens, relevant if the project involves European customers.
- HIPAA (Health Insurance Portability and Accountability Act): US legislation governing the handling of protected health information, relevant for healthcare IT projects.
The WeblineIndia Advantage: Your Assurance of Security and Expertise
While the complexity of ensuring comprehensive data security and IP protection can seem daunting, partnering with a seasoned and trustworthy IT agency is the ultimate solution.
When enterprises decide to hire dedicated developers in India, they are seeking technical excellence, but they also require absolute peace of mind. WeblineIndia is an established IT agency in India, renowned globally for its prowess in mobile app development and web development. With a rich history spanning more than 25 years and a stellar track record of 3500+ completed projects for enterprises around the world, our expertise is built on trust and resilience.
We have integrated global security best practices into our operational DNA, ensuring that our infrastructure and processes proactively mitigate risks before they can escalate.
Our commitment to you includes:
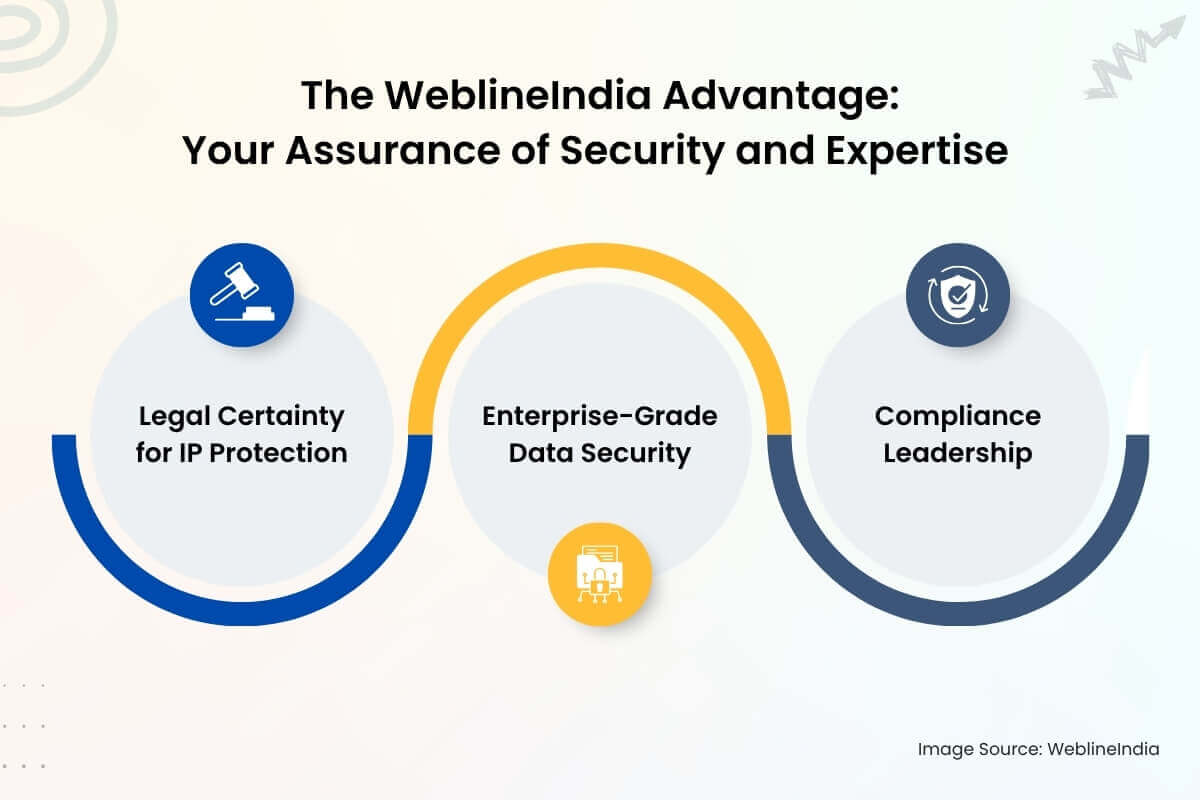
- Legal Certainty for IP Protection: We eliminate all ambiguity regarding ownership. Every contract features explicit, non-negotiable IP assignment clauses, ensuring all code, designs, technologies, and innovations are the exclusive property of the client. Our dedicated developers, who are specially vetted, sign rigorous NDAs and IP transfer agreements, protecting your trade secrets from the ground up.
- Enterprise-Grade Data Security: Our development centers and cloud environments operate under certified data security governance. We strictly enforce international standards, mandatory Multi-Factor Authentication, secure VPN tunnels, and Role-Based Access Control (RBAC) to all project assets, safeguarding your most sensitive information.
- Compliance Leadership: We maintain active compliance with the latest Indian legislation, including the DPDP Act, and are structured to seamlessly meet your international compliance needs (GDPR, HIPAA). Our processes include regular third-party security audits and a mature, tested Incident Response Plan.
Choosing to hire dedicated developers in India through WeblineIndia means selecting a partner that treats your Intellectual Property as sacred. We do not just build software; we build it securely, responsibly, and with guaranteed IP protection. WeblineIndia assures you that your project is in safe and expert hands, allowing you to focus on market execution while we handle the complexity of secure, cross-border development.
Ready to partner with a trusted IT leader who guarantees the security of your innovation? Contact WeblineIndia today to discuss how our robust security framework can support your next project.
Social Hashtags
#DataSecurity #IPProtection #SoftwareOutsourcing #HireDevelopersIndia #OffshoreDevelopment #CyberSecurity #TechCompliance #SecureCoding #SoftwareDevelopment
Want secure, reliable offshore development for your next project? Let’s get started.
Frequently Asked Questions
Testimonials: Hear It Straight From Our Global Clients
Our development processes delivers dynamic solutions to tackle business challenges, optimize costs, and drive digital transformation. Expert-backed solutions enhance client retention and online presence, with proven success stories highlighting real-world problem-solving through innovative applications. Our esteemed Worldwide clients just experienced it.
Awards and Recognitions
While delighted clients are our greatest motivation, industry recognition holds significant value. WeblineIndia has consistently led in technology, with awards and accolades reaffirming our excellence.
OA500 Global Outsourcing Firms 2025, by Outsource Accelerator

Top Software Development Company, by GoodFirms

BEST FINTECH PRODUCT SOLUTION COMPANY - 2022, by GESIA

Awarded as - TOP APP DEVELOPMENT COMPANY IN INDIA of the YEAR 2020, by SoftwareSuggest